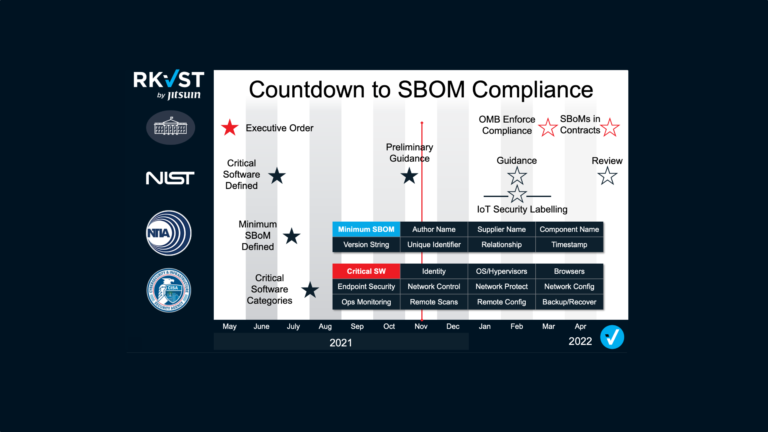
Since the US President’s executive order demanded Software Bills of Material or SBOMs as a key asset to increase cybersecurity and resilience, the term has rapidly moved from software development circles to the boardroom. In our recent blog we examined what IT professionals need to know to implement and share SBOMs effectively – but what do business decision-makers need to know and do to ensure they comply with the Presidential order?
The first thing to note is, whether or not the executive order applies to your business, SBOMs are best practice, and could save you millions. According to security vendor Checkpoint, 87% of organizations have experienced an attempted exploit of an already-known, existing vulnerability in their cyber defences. The lack of controls, evidence, and assurance mean that the number of vulnerabilities is expected to grow from 10,000 per year now to over 50,000 by 2024; many introduced through the software supply chain. With data and digital systems now essential in almost every sector, it is little wonder that the proportion of enterprises looking to use SBOMs will jump from under five percent in 2020 to over sixty percent by 2025! You will be using SBOMs.
NUTRITIONAL LABELLING FOR DIGITAL GOODS
SBOMs have been likened to the nutritional information labels mandated on food and beverages. They are not recipes and won’t provide ways to replicate the products, but they do identify all the constituent ingredients so that consumers can make decisions on the safety and applicability of the product. Publishers of critical software face a legal responsibility to precisely label all the elements that make up their products. As with food and beverages software has expiry dates and the risks associated with individual ingredients can change with time. But, unlike foodstuffs, the ingredients and context of software can change as you consume it! So, unlike a food label, the SBOM is a living document. As developers alter code, integrate new features, or patch vulnerabilities the SBOM must be updated. A precise, up-to-date, accurate SBOM for every product is a business requirement.
SBOMS ALONE SOLVE NOTHING
But making SBOMs is not enough. The whole point of an SBOM is lost if you keep it a secret. Consumers of software, as well as software publishers and vendors, are already beginning to understand the complexity of sharing SBOMs with all the necessary stakeholders in transparent yet secure ways. Although a technology solution, SBOMs are fundamental inputs to core business risk decisions; business audiences must understand how they provide assurance in critical decision-making. Ensuring accurate SBOMs are shared with the right people in the right places at the right time is essential. Having a bad or out-of-date SBOM may create a false sense of security, which could be worse than providing no SBOM at all.
Similarly, software consumers will have a host of SBOMs from multiple different partners and suppliers. Just as restaurants must track every ingredient their chefs use, businesses need to audit all the SBOMs for every piece of software they use. Plus, with software, the ingredients can change while they are on your fork! The complexity of constantly auditing, updating, and integrating SBOMs for hundreds if not thousands of applications across the business goes far beyond what’s possible with manual processes and spreadsheets. Nobody wants to hire an SBOM department.
Enterprises need an automated way to verify then trust SBOMs. Businesses must find effective, robust, and auditable ways for SBOM producers and consumers to collaborate and integrate them into existing business processes. Automated ‘as-a-service solutions are the answer. The RKVST provides Continuous SBOM Assurance including Provenance, Governance, and Immutability to ensure that the right people get the right SBOM information at the right time.
Provenance records the origin of the software. RKVST captures where every component of the software package came from, who is responsible for maintaining the code, and how and when that list of ingredients changes. As code changes, bugs and vulnerabilities are patched or updated, the SBOM must reflect these changes. RKVST alerts business users of SBOM changes so they can identify what’s at risk.
Governance is essential for any critical infrastructure, including software. Clear, precise rules of who is authorized to see what data ensure that sensitive information is available to those that need it and protected from unauthorized access. Current industry and media narratives present a false dichotomy between full transparency and absolute privacy. In truth a nuanced approach is essential. For example, responsible disclosure of vulnerabilities in software must allow time to fix issues before revealing exploitable weaknesses that place some users at risk. RKVST enforces processes that define exactly who sees what, when.
Immutability of the data is paramount to build confidence for automated services that will rely on SBOMs. An unbroken chain of evidence that can prove who did what when, will boost trust in operational decisions for using and deploying SBOMs.
BLOCKCHAIN FOR A GOLDEN THREAD OF EVIDENCE
Using Distributed Ledger Technology (DLT or blockchain as it is commonly known), RKVST provides continuous assurance by automating the management of SBOMs. All changes are irrevocably documented. RKVST is an API driven service. RKVST APIs are used to create and record asset and event information, to define and enforce policies for governing those assets, monitor that the right things are being done, generate alerts and notifications, and produce instant audit and compliance proofs.
Whether your business is a software publisher needing to continuously distribute your SBOM, or a user wanting to automate and alert the business to any relevant changes across the SBOMs representing your software estate, RKVST presents a unified, assured and reliable way to share SBOMs. For more information read our reference implementation guide or to see a demo and example SBOM template service – try it now.