How It Works
Confident decisions through strong provenance and the power of knowing who did what when.
See DataTrails explained in 1 minute
The Power of Provenance
Every decision you make has to be made in the context of your business and your circumstances: given the same data you might make different choices to your partners and suppliers. But one thing is common: all judgments are improved if you can rely on strong historical data.
By keeping a complete and untampered record of “who did what when”, DataTrails® journals the life history of data and documents and attests to their provenance to enable all stakeholders in connected processes to make their own unique risk calculations.
Control in the Right Hands
Traditional data security products often overlap business and technical concerns, forcing business stakeholders to learn data and programming concepts and developers to take more than reasonable responsibility for encoding business rules in code.
DataTrails sets both stakeholders free by providing a simple set-once policy definition interface for business and compliance teams, and a powerful write-once REST interface that allows software integration teams to read and write the data they need without having to worry about data availability, distribution policies, or hard details of cryptography.
One API, Flexible Data Protection
Crucial to maintaining faith in integrity, transparency and trust systems is the concept of immutability: once something has been said it can’t be un-said; once accountable, always accountable.
As part of its hybrid architecture DataTrails uses blockchain to ensure immutability of supply chain history, and gives you the tools you need to ensure that nothing you see has been modified, back-dated, or shredded, even by the DataTrails service itself.
Achieving this immutability with blockchain would traditionally involve a complex set of trade-offs between cost, speed, and size of transactions, but DataTrails makes that easy by having flexible options to suit most situations, all through the same API: from fine-grained individual transactional protection to high-efficiency batching and anchoring.

Discover DataTrails for yourself
Achieve provenance, governance, and immutability for your shared data with none of the costs, distractions and diversions.
Recent Posts
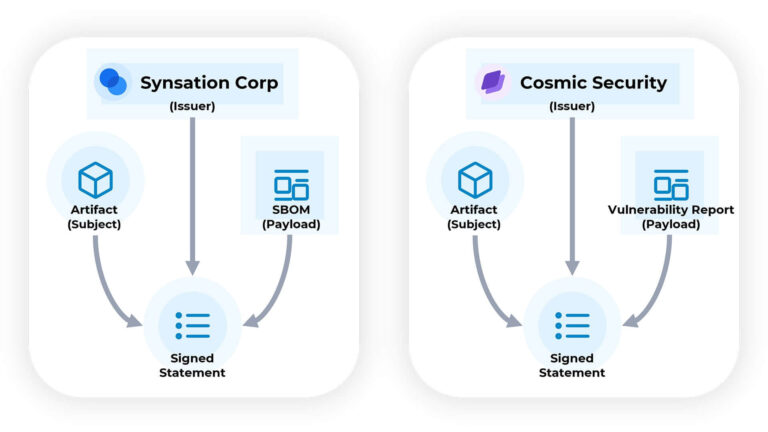
Creating DataTrails for Supply Chain Artifacts
Staying informed about your software means consuming information from various sources and knowing when and where to apply that information.
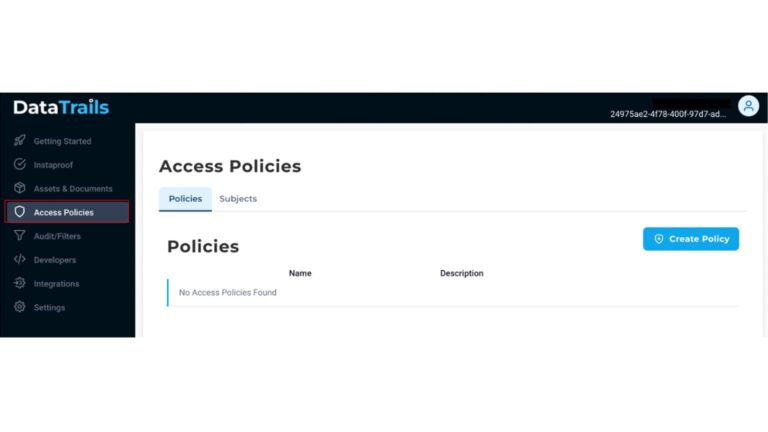
Customize your Access Policies with DataTrails
Signing up with DataTrails comes with the ability to share your audit trails with your business partners, other applications, and your internal team. Access policies control users, apps & organizations’ read & write privileges to provenance…
What is Data Provenance?
Everything you need to know about Data Provenance Data provenance is a technology field that aims to help businesses increase trust through transparency of data, specifically by tracking the origin, change, and history of data and…