Let’s start at the beginning. What is Zero Trust?
Trust is a very broad and complex topic, and consequently there are very many definitions of Zero Trust that can be confusing as they try to capture the nuance and details and scope that the problem of trust raises. However, Microsoft’s article “Evolving Zero Trust” from November 2021 captures the concept well:
“Zero Trust is a proactive, integrated approach to security across all layers of the digital estate that explicitly and continuously verifies every transaction, asserts least privilege, and relies on intelligence, advanced detection, and real-time response to threats.”
It’s worth breaking out these key points and exploring why they’re important: in most cases these serve to highlight where Zero Trust differs from traditional cyber security approaches, and in so doing explain why change is needed.
- Proactive: All components of the system are responsible for knowing what security and trust requirements they have, and how to check them. This is in contrast to traditional or network security approaches where a lot of software assumes that any data or user on the inside is authorized and trustworthy.
- Approach: Zero Trust is a way of evaluating and addressing the questions of security and trustworthiness, not a magic security box or cyber widget that you can simply buy and install.
- Integrated & Intelligence: Trust and security are system issues, not component ones: all the parts of your system need to be able to work together to achieve a business outcome. This doesn’t happen if all the parts have different security models or can’t interoperate.
However, risk decisions are individual and subjective: different businesses will make different decisions even given the same set of facts. And decisions can always be improved with more data – so long as those data can be trusted. In traditional silo network security models, the relevant information to make the right security decision probably exists somewhere in the system but is locked away and not available to the component that needs it in the moment, but Zero Trust drives better outcomes through collaborative sourcing and sharing of the best available context information throughout connected systems and supply chains.
- Continuous: Traditional assurance depends on point-in-time audits and certification, often based on outdated static criteria, and verified once a year at best. But to deal with the latest intelligence and make the best possible decisions we need to move to a model of continuous assurance where systems are constantly verifying that they still meet the safety and security promises they were designed for.
- Real–time: Situations change all the time. Things are only secure until they’re not, and even the simple passage of time may render a previously trustworthy device dangerous if vulnerabilities are discovered or the economics of attack change. All decisions need to be made in the current context or what you’re doing, with whom, and how risky it is right now.
A Zero Trust approach does not mean that there is no trust. Instead, it aims to increase trust in the system by driving down toward zero all the assumptions, shortcuts, and blind spots that came with traditional network security approaches.
It’s not “trust but verify”; it’s “always verify then trust”.
What is Zero Trust Architecture?
Zero Trust Architecture is an approach to building software and data infrastructure that can operate on Zero Trust principles, and when it comes to building systems the number one core principle of Zero Trust is to “assume breach”.
Traditional network security approaches try to prevent intruders from getting in by deploying edge firewalls, perimeter ID verification, and data-in-transit encryption, but then leave internal systems open to attack hoping that the perimeter defence holds up. But the reality is that these systems can only do so much and will be breached eventually, so the Zero Trust approach focuses less on pure prevention and more on detecting problems and staying resilient when (not if) a breach occurs.
Rather than being implemented in point solutions or in edge firewalls, security and trustworthiness verification is interwoven with operations, not a ‘thing’ or widget that can simply be bought and installed.
A happy side-effect of all of this is that a Zero Trust approach makes systems resilient to all kinds of faults such as mistakes, accidents, misconfigurations and the like: all many common things that can harm digital operations but are not actually attacks and therefore often not caught by defence-only permitter approaches.
Why do we need a Zero Trust Fabric?
Zero Trust Fabric is the missing link in enabling businesses to adopt Zero Trust without the need to rip out all their existing infrastructure and start again. Lest it be unclear, traditional defensive network products are not necessarily bad, they’re just insufficient to deal with the reality of today’s highly connected operations and highly dynamic risk landscape. While some organizations may have the luxury of creating a completely green field Zero Trust architecture for their data operations, most will need to evolve into it by augmenting legacy systems with Zero Trust goodness.
The Zero Trust Fabric enables this by creating a safe ‘bridge’ for critical information to flow between organisations and across boundaries in a secure and verifiable manner.
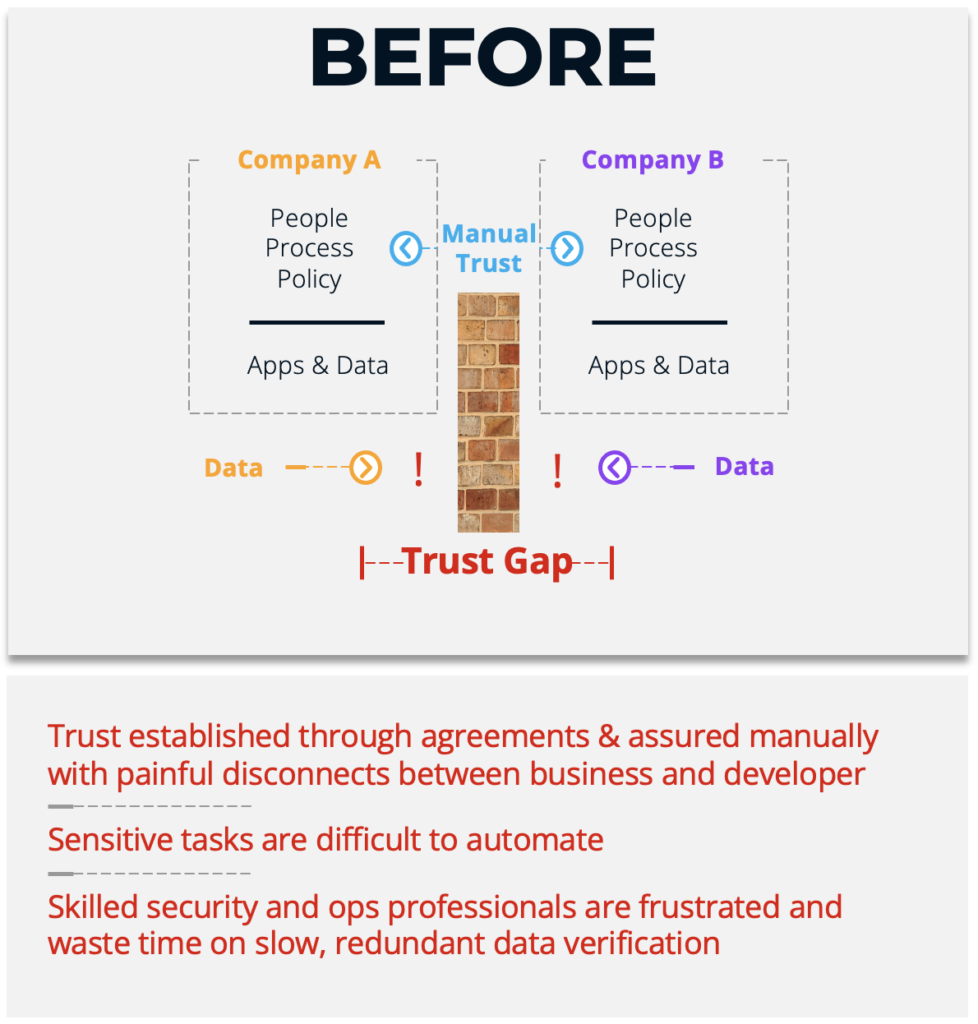
The traditional fortress model of network security does a great job of keeping information inside individual silos, but this also means that distributing crucial supply chain intelligence is doubly hard: sharing information with partners actually requires breaking through the security mechanisms, deploying shadow IT, or engaging in lossy, unreliable manual copy processes.
When so much crucial operating intelligence originates outside of organizations – either from specialist suppliers or supply chain partners – this friction in getting reliable data to the right place at the right time severely inhibits connected operations. And where data cannot flow at all, blind spots appear, and decisions are detrimentally affected. Getting the best available system-wide risk intelligence to the place where it’s needed on time, every time, is a tough problem.
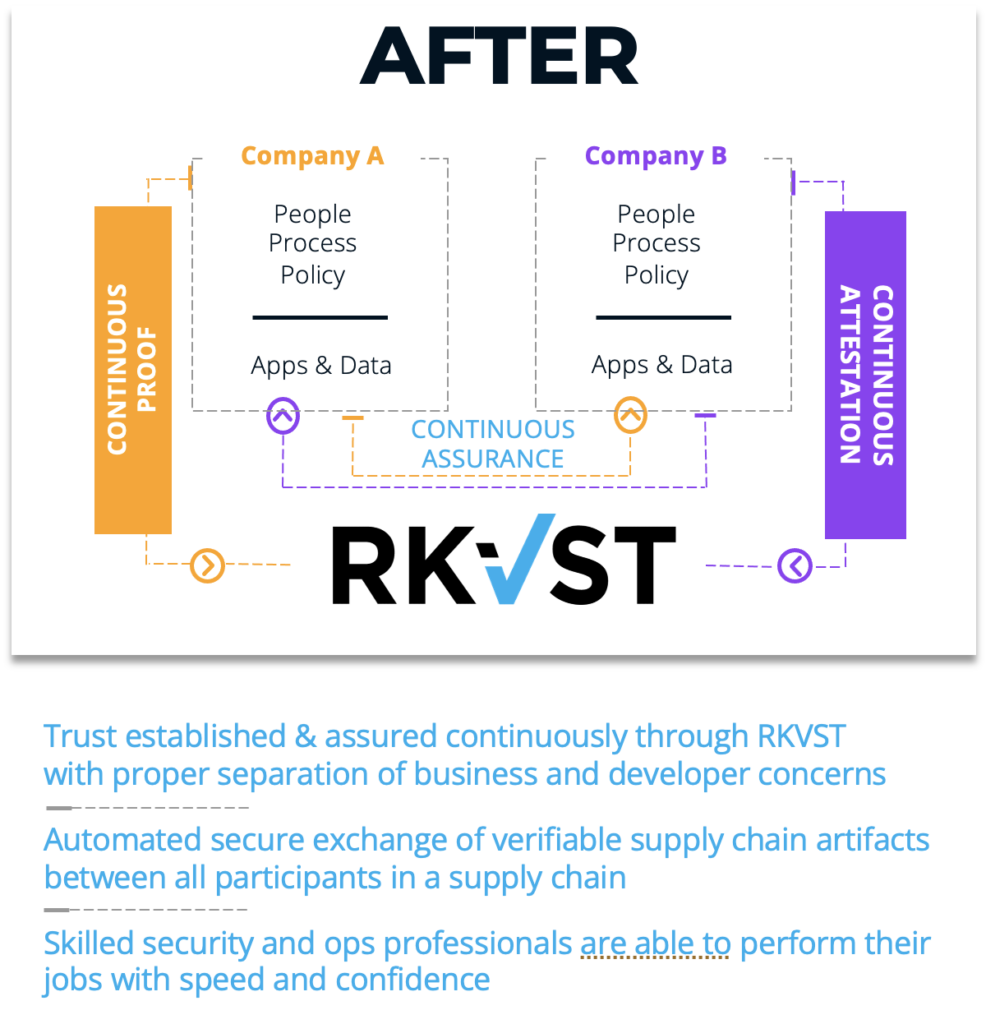
The Zero Trust Fabric unlocks the potential of digital transformation and brings efficiency to supply chain operations by enabling visibility of necessary data between supply chain partners, while leaving existing private operations alone.
All data flowing through the Zero Trust Fabric is protected with strong Provenance, Governance, and Immutability guarantees to make it reliable and trustworthy for ingestion in your applications and processes almost as if you had generated it yourself.
In addition to the real-time visibility of information from partners, the Zero Trust Fabric maintains a complete tamper-proof lifecycle history of all data objects in the system, creating a golden thread of evidence for digital operations and fitting right in with existing audit and regulatory processes.
Where do I go from here?
If you want to improve efficiency and reliability of your digital supply chain, need to improve visibility of risk information, or are struggling to fully realise the potential of digital transformation and automation because unreliable or untrustworthy supply data, a Zero Trust Fabric could be the service for you. Visit https://rkvst.com to learn more.